In response to the rising demand for protecting sensitive data, Transcend now offers industrial SSDs that conform to TCG Opal 2.0 standards and IEEE 1667 specifications.
Transcend Information : TCG Opal SSDs Bring Driving Forces To Elevate Data Storage Security
What is the TCG Opal Storage Specification?
The Trusted Computing Group (TCG) is an organization whose members work together to formulate industry standards, which it then makes public for use by those in industry.
TCG’s Storage Work Group created the Opal Security Subsystem Class (SSC) as one class of security management protocol for storage devices. It applies mainly to devices used in PCs and notebooks. The class defines specifications concerning file management on storage devices, and defines class level permissions for storage/retrieval of files, thus protecting user data. Devices conforming to Opal SSC specifications may be referred to as TCG Opal devices, a mark of trustworthiness.
TCG Opal 2.0 standards cover the manufacture of storage devices, system installation, and management. It secures sensitive data via password setting and sector-specific management, so corporate clients can rest assured that their data is protected at an advanced security level.
TCG Opal Features
Opal is a comprehensive set of guidelines. The target audience includes manufacturers of storage devices, software vendors, system integrators, and academia. These specifications cover the manufacture of storage devices, system setup, management, and use; they allow for password protection and hierarchical storage management, while preventing data from being stolen or tampered with.
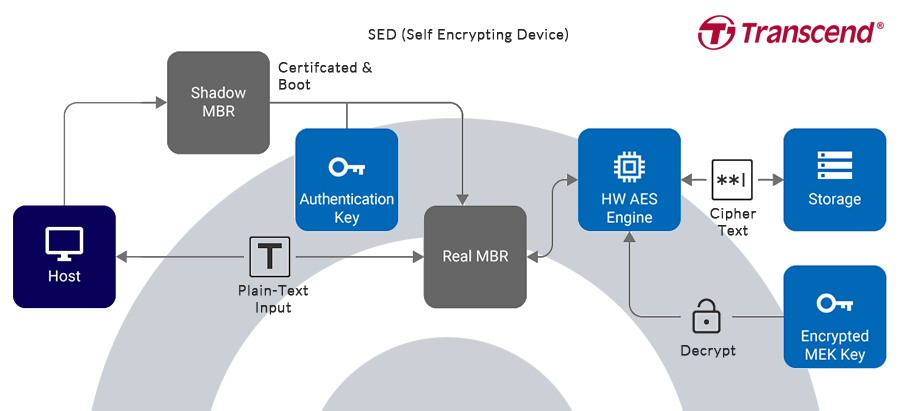
Storage devices complying with Opal SSC specifications feature the following:
- They are self-encrypting devices: Data encryption is performed on the device, without need to pass through the host. The encryption key is also stored on the device (commonly 128-bit or 256-bit AES is utilized).
- They feature boot authentication: When the user starts the device, the shadow MBR will conduct a pre-boot identification; where the user is cleared, the normal boot process will begin and connections to devices be made.
- They allow for sector specific permissions: The device manager may create a logical block address (LBA) range and assign different permissions for each LBA range. Only users with the correct key for a particular LBA range may perform permitted actions. Where drive locations are password-protected, only users with the correct key will be authorized entry.
- Each range can be erased independently and cryptographically. Where erasure takes place, the original MEK key is destroyed, and a new key is generated.
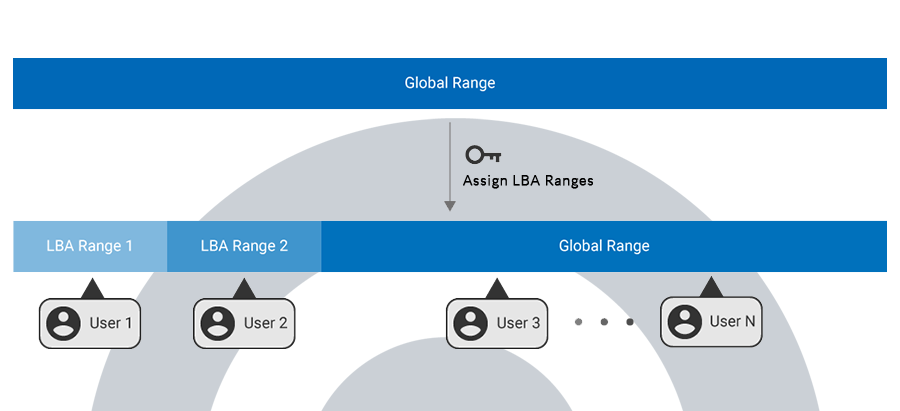
What are the Advantages to Opal ?
In a hierarchically managed system, only authorized users may access data on a device to which they have added password protection; this minimizes the chance of data being stolen, tampered with, or lost.
All security functions take place within the device itself. They do not need to pass through the host (operating system); they do not utilize system resources, making for faster and more secure operation and preventing operating system compatibility issues.
Information security is equally important for both business and personal users. Today, security is a growing concern as greater amounts of data are being created and utilized. The TCG designed Opal to address both software and hardware approaches to security, and the need for hierarchical management. From the manufacturer to the user, Opal is a standard that serves the needs of everyone.
Transcend’s AES SSDs are compliant with the TCG Opal 2.0 standards, and can be customized by request to meet specific customer needs.
Transcend Industrial TCG Opal SSDs
In response to the rising demand for protecting sensitive data, Transcend offers industrial SSDs that conform to TCG Opal 2.0 standards and IEEE 1667 specifications. Compliant with these international security guidelines, the SSDs are strengthened by the Advanced Encryption Standard (AES) 256-bit hardware-based encryption, and support Microsoft eDrive functionality.
Features
- Self-encrypting device (SED): The entire encryption process is carried out on the drive itself, not affecting host system.
- Pre-boot authentication verifies user identity before normal boot process.
- Sector-specific permissions: Manager can assign different permissions for different drive sectors.
- Cryptographic keys are randomly generated, highly secured and hard to decipher.
- TCG Opal Toolbox security software provides quick password setting and hierarchical storage management.
Target Applications
- Ruggedized Computing
- Healthcare Carts
- Digital Entertainment
- Image Surveillance Systems
- Smart Manufacturing Systems
Transcend’s recently released industrial-grade TCG Opal encrypted solid-state drives (SSDs), elevate data security in an era of big data in which information is being collected and transmitted on vast scales, complying with the TCG Opal 2.0 standards and IEEE 1667 specification.
Transcend’s TCG Opal SSDs support Microsoft eDrive functionality, delivering industry-leading security to high-end applications including defence, finance, digital entertainment and smart healthcare.
Transcend’s Opal-compliant SSDs incorporate hardware-based AES 256-bit encryption; ensuring data is safeguarded starting from the manufacture of the storage device to system installation and management. As a self-encrypting device (SED), the TCG Opal SSDs will not impact host performance since encryption and decryption are conducted on the drives themselves instead of the host system, increasing the system speeds while mitigating data security risks.
In a world of high-performance computing, keeping data safe is crucial to organisations and enterprises, these Opal-compliant SSDs offer sector-specific security, allowing managers to grant different permissions to different users to ensure compartmentalized data security.
The SSDs also feature pre-boot authentication, meaning they can only be booted when the user is verified, preventing unauthorized access. Transcend also provides the TCG Opal Toolbox where password-setting and sector-specific permissions can be managed to enhance management efficiency on large deployments.
Transcend Industrial-grade TCG Opal SSDs
| Interface | Form Factor | Product | DRAM | Capacity |
| NVMe PCIe Gen4 x4 | M.2 2280 | MTE712A | With DRAM | 256GB-2TB |
| NVMe PCIe Gen3 x4 | M.2 2280 | MTE672A | DRAM-less | 128GB-1TB |
| NVMe PCIe Gen4 x4 | M.2 2280 | MTE560I (Coming Soon) | With DRAM | 80GB-640GB |
| NVMe PCIe Gen3 x4 | M.2 2242 | MTE470A | DRAM-less | 128GB-1TB |
| SATA III 6Gb/s | M.2 2280 | MTS970A (Coming Soon) | With DRAM | 128GB-2TB |
| SATA III 6Gb/s | 2.5″ | SSD470A (Coming Soon) | With DRAM | 256GB-4TB |










